CVE-2025-32462 , CVE-2025-32463 Sudo chroot, host Option Elevation of Privilege Vulnerabilities
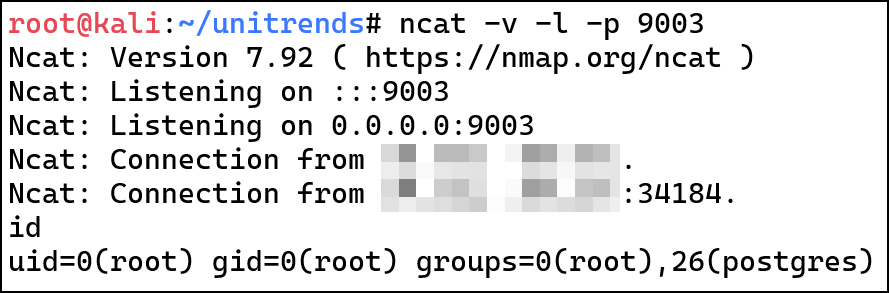
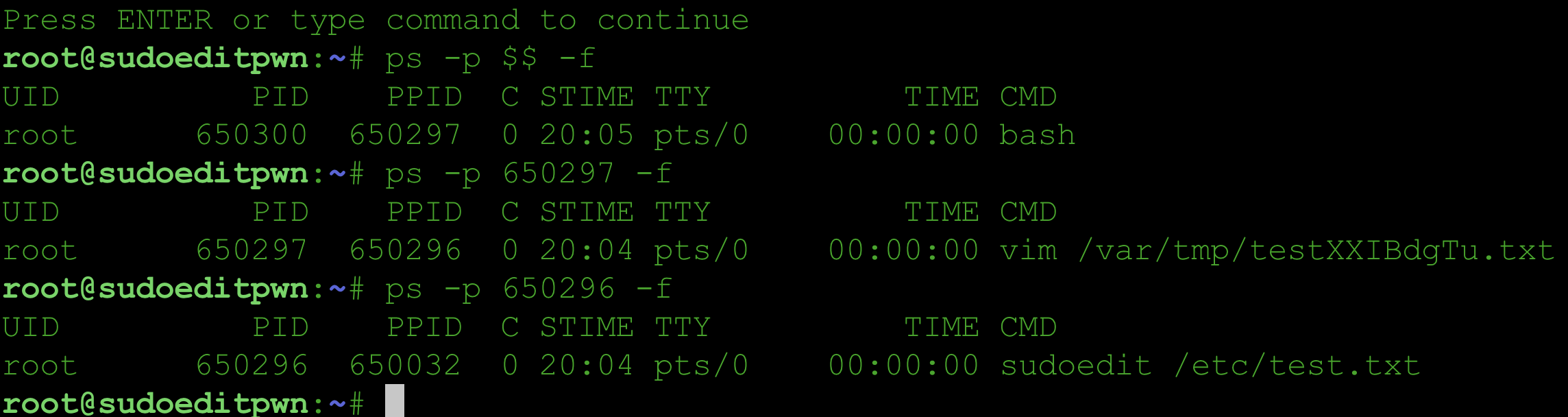
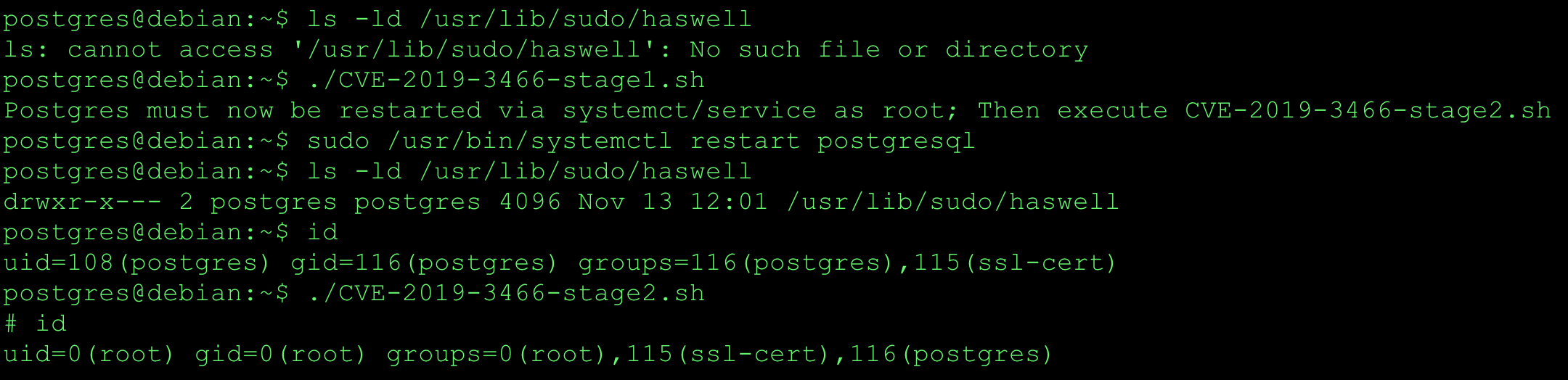
I discovered two vulnerabilities in Sudo. Upgrade to Sudo 1.9.17p1 or later. CVE-2025-32462 - Sudo Host Option Elevation of Privilege Vulnerability CVE-2025-32462 has remained unnoticed for over 12 years, despite being present in the code all along. It relies on a specific yet common configuration where Sudo rules are restricted to certain hostnames or hostname patterns. If these conditions are met, privilege escalation to root requires no exploit. Write-up: Sudo Host Option Elevation of Privilege Advisories Sudo: https://www.sudo.ws/security/advisories/host_any/ RedHat: https://access.redhat.com/security/cve/cve-2025-32462 Ubuntu: https://ubuntu.com/security/notices/USN-7604-1 Debian: https://lists.debian.org/debian-security-announce/2025/msg00118.html Amazon: https://explore.alas.aws.amazon.com/CVE-2025-32462.html Gentoo: https://bugs.gentoo.org/show_bug.cgi?id=CVE-2025-32462 CVE-2025-32463 - Sudo chroot Elevation of Privilege Vulnerability CVE-2025-32463 The default Sudo configuration is vulnerable. Although the vulnerability involves the Sudo chroot feature, it does not require any Sudo rules to be defined for the user. As a result, any local unprivileged user could potentially escalate privileges to root if a vulnerable version is installed. ...