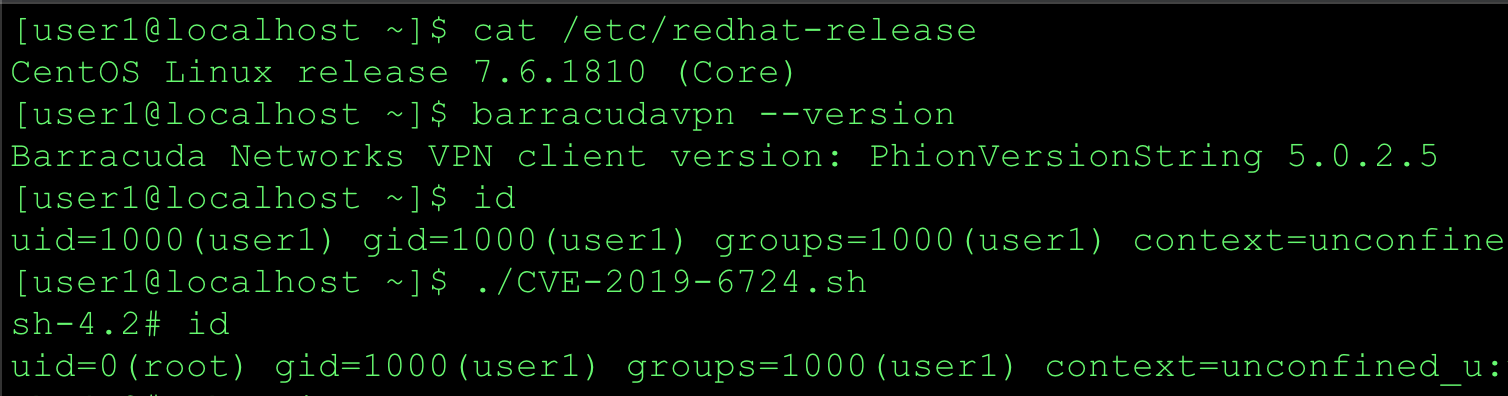
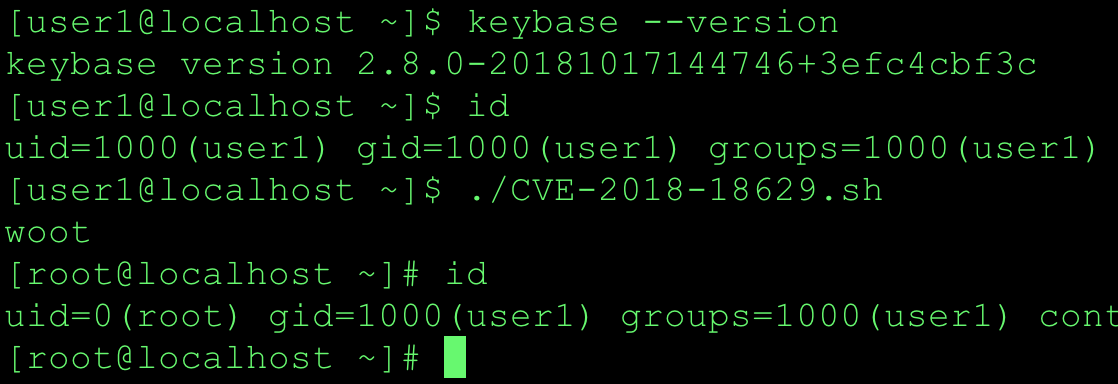
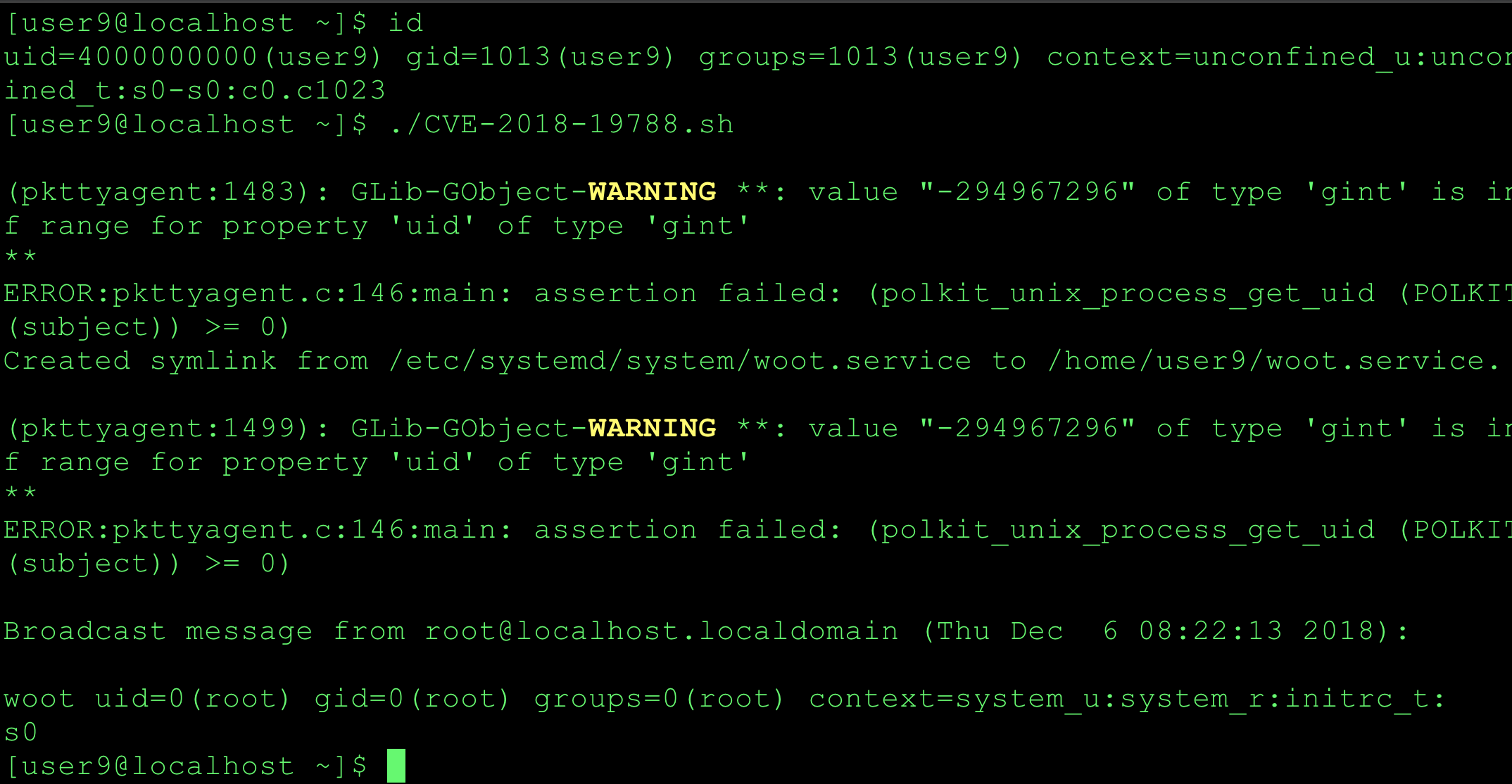
CVE-2019-12572 PIA Windows Privilege Escalation: Malicious OpenSSL Engine
Vulnerability Summary During startup the PIA Windows service(pia-service.exe) loads the OpenSSL library from C:\Program Files\Private Internet Access\libeay32.dll. This library attempts to load the C:\etc\ssl\openssl.cnf configuration file. By default on Windows systems, authenticated users can create directories under C:\. A low privileged user can create a openssl.cnf configuration file to load a malicious OpenSSL engine library resulting in the arbitrary code execution as SYSTEM when the service starts. The root cause is when the OpenSSL libraries were built, the OPENSSLDIR parameter was set to a path which a low privileged user can modify or create. I believe this issue is lurking in many Window applications that bundle OpenSSL libraries. I have discovered the same vulnerability in several other Windows applications and will be disclosing those findings when patches are available. I created a simple tool to help identify potentially vulnerable OpenSSL libraries - https://github.com/mirchr/openssldir_check. CVE-2019-12572 has been patched in v1.2.1. The latest Windows desktop client can be upgraded automatically via the application or manually from the download page at Private Internet Access. Walkthrough While hunting for potential vulnerabilities in the Windows Private Internet Access desktop application I noticed a failed call to open the c:\etc\ssl\openssl.cnf file during the service startup. This caught my attention and I needed to research this further. But before I get into the details of that, let’s take a step back and see how I arrived there.